A Georgia-based pipeline company had to shut down its East Coast oil and gas pipeline this weekend following a ransomware cyber attack.
The FBI has confirmed that the “Darkside” ransomware is responsible for the compromise of the Colonial Pipeline networks. The agency said they will continue to work with the company and the government on the investigation.

Unconfirmed reports indicate the ransomware may be linked to a Russian cybercrime gang also called “Darkside”.
How does ransomware work?
According to the Cybersecurity and Infrastructure Security Agency, ransomware is an ever-evolving form of malware designed to encrypt files on a device, rendering any files and the systems that rely on them unusable. Malicious actors then demand ransom in exchange for decryption. Ransomware actors often target and threaten to sell or leak exfiltrated data or authentication information if the ransom is not paid. In recent years, ransomware incidents have become increasingly prevalent among the Nation’s state, local, tribal, and territorial (SLTT) government entities and critical infrastructure organizations.

On Sunday, the U.S. Department of Transportation (USDOT) issued an emergency declaration which allows for alternative transportation routes for oil and gas to avoid disruption to supply.
The USDOT’s Federal Motor Carrier Safety Administration (FMCSA) is taking steps to create more flexibility for motor carriers and drivers by issuing a temporary hours of service exemption that applies to those transporting gasoline, diesel, jet fuel and other refined petroleum products to Alabama, Arkansas, District of Columbia, Delaware, Florida, Georgia, Kentucky, Louisiana, Maryland, Mississippi, New Jersey, New York, North Carolina, Pennsylvania, South Carolina, Tennessee, Texas and Virginia.
Click here for the full text of FMSCA’s action.
In a press briefing Monday, Homeland Security Advisor Elizabeth Sherwood-Randall said there is enough oil and gas in supply to give the company time to become operational. “Right now there is not a supply shortage. We are preparing for multiple possible contingencies because that’s our job,” said Sherwood-Randall. “We are also considering what additional steps may be useful to mitigate any potential disruptions to supply.”
“Thus far, Colonial has told us it has not suffered damage and can be brought back online relatively quickly, but that safety is a priority given that it has never before taken the entire pipeline down,” Sherwood-Randall added. “This weekend’s events put the spotlight on the fact that our nation’s critical infrastructure is largely owned and operated by private-sector companies. When those companies are attacked, they serve as the first line of defense, and we depend on the effectiveness of their defenses.”
The pipeline transports over 100-million gallons of fuel daily along the east coast.
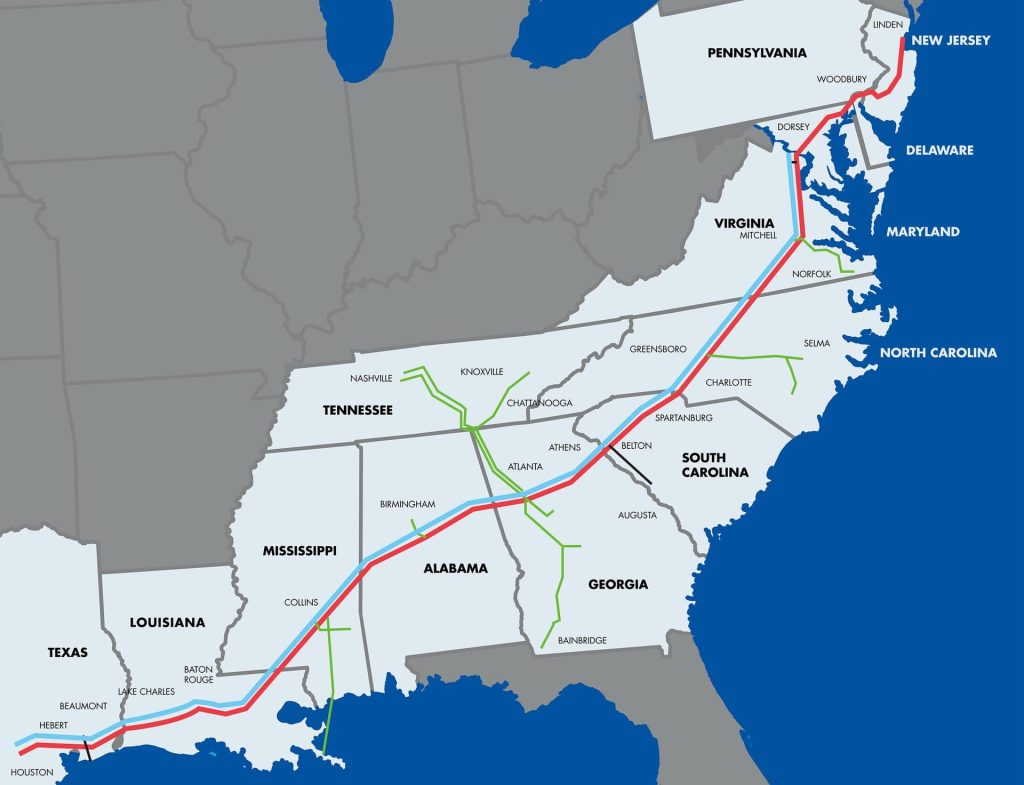
What follows is a timeline of events as provided by Colonial Pipeline:
Saturday, May 8, 12:30 p.m.
On May 7, the Colonial Pipeline Company learned it was the victim of a cybersecurity attack. We have since determined that this incident involves ransomware. In response, we proactively took certain systems offline to contain the threat, which has temporarily halted all pipeline operations, and affected some of our IT systems. Upon learning of the issue, a leading, third-party cybersecurity firm was engaged, and they have launched an investigation into the nature and scope of this incident, which is ongoing. We have contacted law enforcement and other federal agencies.
Colonial Pipeline is taking steps to understand and resolve this issue. At this time, our primary focus is the safe and efficient restoration of our service and our efforts to return to normal operation. This process is already underway, and we are working diligently to address this matter and to minimize disruption to our customers and those who rely on Colonial Pipeline.
Sunday, May 9, 5:10 p.m.
On May 7, Colonial Pipeline Company learned it was the victim of a cybersecurity attack and has since determined that the incident involved ransomware. Quickly after learning of the attack, Colonial proactively took certain systems offline to contain the threat. These actions temporarily halted all pipeline operations and affected some of our IT systems, which we are actively in the process of restoring.
Leading, third-party cybersecurity experts were also immediately engaged after discovering the issue and launched an investigation into the nature and scope of this incident. We have remained in contact with law enforcement and other federal agencies, including the Department of Energy who is leading the Federal Government response.
Maintaining the operational security of our pipeline, in addition to safely bringing our systems back online, remain our highest priorities. Over the past 48 hours, Colonial Pipeline personnel have taken additional precautionary measures to help further monitor and protect the safety and security of its pipeline.
The Colonial Pipeline operations team is developing a system restart plan. While our mainlines (Lines 1, 2, 3 and 4) remain offline, some smaller lateral lines between terminals and delivery points are now operational. We are in the process of restoring service to other laterals and will bring our full system back online only when we believe it is safe to do so, and in full compliance with the approval of all federal regulations.
At this time, our primary focus continues to be the safe and efficient restoration of service to our pipeline system, while minimizing disruption to our customers and all those who rely on Colonial Pipeline. We appreciate the patience and outpouring of support we have received from others throughout the industry.
Monday, May 10, 12:25 p.m.
Colonial Pipeline continues to dedicate vast resources to restoring pipeline operations quickly and safely. Segments of our pipeline are being brought back online in a stepwise fashion, in compliance with relevant federal regulations and in close consultation with the Department of Energy, which is leading and coordinating the Federal Government’s response.
Restoring our network to normal operations is a process that requires the diligent remediation of our systems, and this takes time. In response to the cybersecurity attack on our system, we proactively took certain systems offline to contain the threat, which temporarily halted all pipeline operations, and affected some of our IT systems. To restore service, we must work to ensure that each of these systems can be brought back online safely.
While this situation remains fluid and continues to evolve, the Colonial operations team is executing a plan that involves an incremental process that will facilitate a return to service in a phased approach. This plan is based on a number of factors with safety and compliance driving our operational decisions, and the goal of substantially restoring operational service by the end of the week. The Company will provide updates as restoration efforts progress.
We continue to evaluate product inventory in storage tanks at our facilities and others along our system and are working with our shippers to move this product to terminals for local delivery. Actions taken by the Federal Government to issue a temporary hours of service exemption for motor carriers and drivers transporting refined products across Colonial’s footprint should help alleviate local supply disruptions and we thank our government partners for their assistance in resolving this matter.
Our primary focus continues to be the safe and efficient restoration of service to our pipeline system, while minimizing disruption to our customers and all those who rely on Colonial Pipeline. We appreciate the patience of the traveling public and the support we have received from the Federal Government and our peers throughout the industry.







